# Understanding the Distinction Between HTTP and HTTPS
Written on
Chapter 1: Introduction to HTTPS
The question of how HTTPS differs from HTTP may seem outdated, yet I often encounter non-technical friends who still seek clarification. Initially, my knowledge was limited to the fact that HTTPS employs asymmetric cryptography, a concept I grasped during my studies. However, I decided to explore the subject further.
In essence, HTTPS serves as an enhanced version of HTTP, represented as follows:
HTTPS = HTTP + SSL/TLS.
SSL, or Secure Sockets Layer, and TLS, or Transport Layer Security—its successor—are both protocols that ensure the security of data in transit. In contrast to HTTP, where data may appear as plain text, HTTPS encrypts this information, making it unreadable without proper decryption.
For instance, with HTTP, you might see:
This is a plaintext message.
Whereas with HTTPS, the data looks something like this:
dg5e6fd465h76ea8g4wa23g132a1b
This encryption makes it significantly more challenging for potential attackers to decipher the actual data being transmitted. So how does HTTPS function?
To illustrate, a diagram can be quite beneficial.
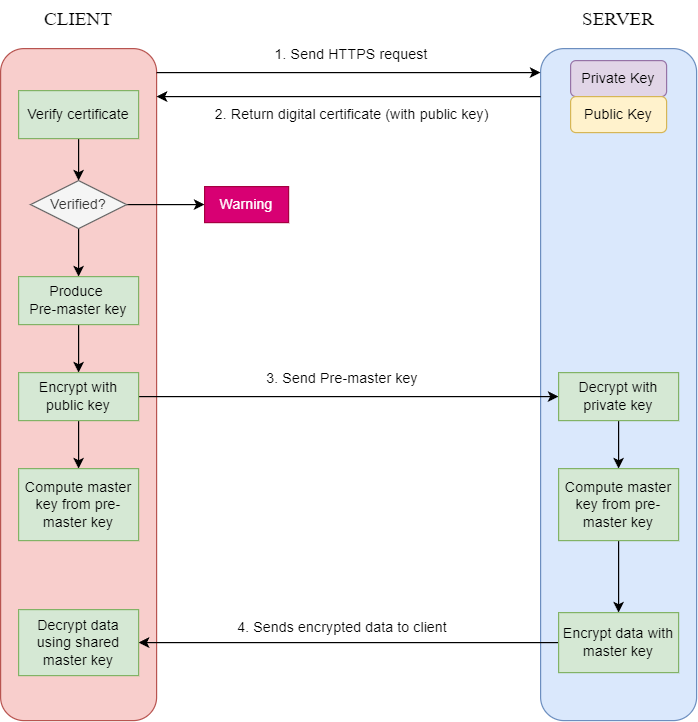
Firstly, when a client initiates an HTTPS request, it connects to the server through port 443 (Step 1). The server possesses a digital certificate that includes the public key, the certificate issuer, and its expiration date. It then sends this certificate back to the client (Step 2).
What is a Public Key?
Public key cryptography involves a pair of keys: a public key, which is accessible to everyone in the network, and a private key, which remains confidential. The public key encrypts data sent to the recipient, who can then use the private key to decrypt it, ensuring data security and privacy.
Upon receiving the certificate, the client verifies its authenticity. If the certificate is valid, the client generates a random pre-master key, encrypts it using the server’s public key, and sends it back to the server (Step 3). The server, having the private key, can then decrypt this pre-master key.
Now both the client and server have access to the pre-master key. They will use this key, along with the agreed-upon cipher suite, to create a symmetric master key.
What is a Symmetric Master Key?
The symmetric master key is utilized during a network session between the client and server. Unlike the earlier public-private key pair, this key is part of a different cryptographic method—symmetric-key algorithms. In this case, both encryption and decryption depend on the same key.
Once the master key is established, the client and server can exchange information securely, with no one else able to decipher the transmitted data.
Does this sound complex?
HTTPS exemplifies a scenario where both asymmetric and symmetric cryptography work in tandem, ensuring secure data communication over the network.
What do you think? Feel free to share your thoughts in the comments below.
I hope you find this article informative. As a backend software engineer, I encourage those interested in technology to follow my channel for updates and insights drawn from my daily experiences in the field.
Read More:
- A Case About Java Static Keyword During My Job
- How Can You Solve This Java Multithreading Interview Problem?
Get Connected:
- My LinkedIn
Chapter 2: Videos Explaining HTTP and HTTPS
The first video titled "What Is The Difference Between HTTP & HTTPS? (What Is A SSL Certificate?)" provides an insightful overview of the key distinctions and the role of SSL certificates in web security.
The second video, "What is the difference between HTTP and HTTPS protocol?" further elaborates on these differences, making it a valuable resource for understanding web security.